The intrusion detection system or IDS is a software product or device designed to detect unauthorized and malicious activity on an organization’s computer network or a separate host.
The task of the intrusion detection system is to detect and prohibit the penetration of cybercriminals into the IT infrastructure and generate a security alert. However, if there are no response functions, such as blocking unwanted activity, it will be transmitted to the SIEM system for further processing.
The organization’s intrusion detection system is way different from regular firewalls. The latter relies on static rules and restricts traffic between devices or network segments without sending notifications. The development of the IDS idea is the intrusion prevention system (IPS, intrusion prevention systems), which can fix and block threats.
The main features of the intrusion detection system includes:
- detection of intrusions and network attacks;
- recording of all events;
- Search for vulnerabilities;
- predicting attacks;
- identifying the source of the attack: insider or hacking;
- informing information security services about the incident in real-time;
- Generation of reports.
Also Read: HOW TO MANAGE A RETAIL STORE WITH POS TECHNOLOGY
Intrusion detection network composition
The main parts of the IDS include:
- a reading subsystem that accumulates information from the network,
- the analyzing part of the system that detects attacks or malicious actions,
- a database that stores all information about collected data, attacks, analysis, etc.,
- a control system with which the user can set the criteria for the entire system’s operation, view the network, delimit access to view attacks, analysis reports.
IDS classification
Intrusion detection systems are usually classified according to the scope of their use. The following types of IDS are available for the use of massive corporates:
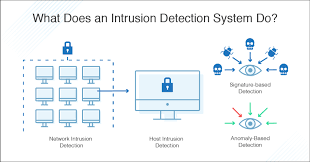
- Network Intrusion Detection System (NIDS) – This system analyzes network traffic to detect malicious activity. Unlike firewalls, NIDS monitors both inbound and internal network traffic.
- Host Intrusion Detection System (HIDS) – These tools monitor the operation of individual devices. It captures the state of all files hosted on the endpoint and informs the administrator about the removal or modification of system objects. Also, HIDS can check all data packets sent to or from the device.
- Protocol-based Intrusion Detection System (PIDS)- It is a systen generated to check data transmitted over the HTTP / HTTPS protocol. Most often these are used to protect web servers and control traffic transmitted between the user’s device and the Internet resource.
- Application Protocol-based Intrusion Detection System (APIDS)- This is an intrusion detection system that monitors packets transmitted over a specific application layer protocol – for example, specified for accessing a SQL database.
- The Hybrid Intrusion Detection System- This is a modern hybrid system for comprehensive malware detection that combines the properties of two or more of the above types, such as NIDS and HIDS.
How IDS works
Intrusion detection systems detect malicious activity using one of the following methods:
- Signature-based detection: It is a process in which intrusion detection systems validate data with known patterns of attack signatures and generate a security alert if they match. It allows them to detect intrusions that are based on previously known penetration methods.
- Detection based on anomalies: With detection based on anomalies, IDS compares the activity on the network or on the host with the model of correct, trusted behaviour of the monitored elements and records deviations from it. This method allows an organization to identify new threats easily.
Also Read: TOP 10 MOBILE APPS TO MANAGE YOUR WORDPRESS SITE
When are network attack detection systems used?
From an organization’s experience, the network intrusion detection system must work round the clock. Those corporates that neglect solutions for detecting and suppressing attacks incur maximum losses. Recently sensational ransomware viruses “Petya and Wanna Cry” caused havoc and paralyzed the activities of multiple organizations. Since the rate of attacks is only increasing every year, decisions on their detection should be one step ahead to be able not only to investigate incidents but also to prevent them at the first sign in real-time.
Requirements for IDS / IPS systems
In India, the requirements for intrusion detection systems appeared in the last decade. Nowadays, there are multiple intrusion detection systems with differences in the level of information systems and the information itself to be processed like personal data, confidential information, company secrets. The regulatory compliance is also a must-have while choosing an intrusion protection solution for your company.
Advantages of Intrusion Detection System Implementation
These systems are mostly used in an enterprise, as it allows them to monitor at what point an attack or illegal entry began. In addition, it also provides the ability to track the behavior and actions of a third-party visitor. It can easily store and display everything that this person did from the moment of logging in to the system to causing harm
The intrusion detection system will also notify the user if the data has been deleted or changed. It allows corporations to improve the integrity of its system. In the event of any network failure, a company can easily detect what happened and where.
These systems can also scan the Internet resources and determine when and where the system was logged in. However still, their performance is limited, and they cannot determine some actions.
For example, if you have a problem with network protocols, if logging into the company employees’ system is simple, then such systems cannot see intruders. However, it should be noted that the system can not cope with all the problems of entry. For example, with packet layer attacks, they fail.
Solution for comprehensive network protection, detection and suppression of network attacks
There are multiple intrusion detection systems available as a hardware and software complex for investigating network incidents at the level of traffic packets, which allows finding vulnerabilities in the company’s network infrastructure. They work by recording and decoding all events in the organization’s network, finding those responsible for any security incident, and preventing it.
Another solution is to scale well for wide area networks, which allows an organization to protect the network infrastructure in an integrated manner. It also allows them to see everything that happens on the network in real-time, identifying all types of intrusions and instantly preventing attacks. All this is possible thanks to modern softwares that can perform continuous analysis of events and detect deviations from the normal behavior of users and systems on the network.
Also Read: HOW IOT HAS AN IMPACT ON VARIOUS INDUSTRIES